Ten Tips for Making the Best Use of AI Chatbots
Since ChatGPT launched in late 2022, people have been using AI chatbots to brainstorm, speed up research, draft content, summarize lengthy documents, analyze data, assist with writing and debugging code, and translate text into other languages. Recently, the major chatbots have gained Web search capabilities, allowing them to access live information beyond their training model data.
Using a chatbot effectively requires new approaches to thinking and working, especially when it comes to searching for information. Just as with a human assistant, you need to play to their strengths when figuring out the best ways to get the results you want. Incorporate these tips into your chatbot conversations, and you’ll see significantly better outcomes.
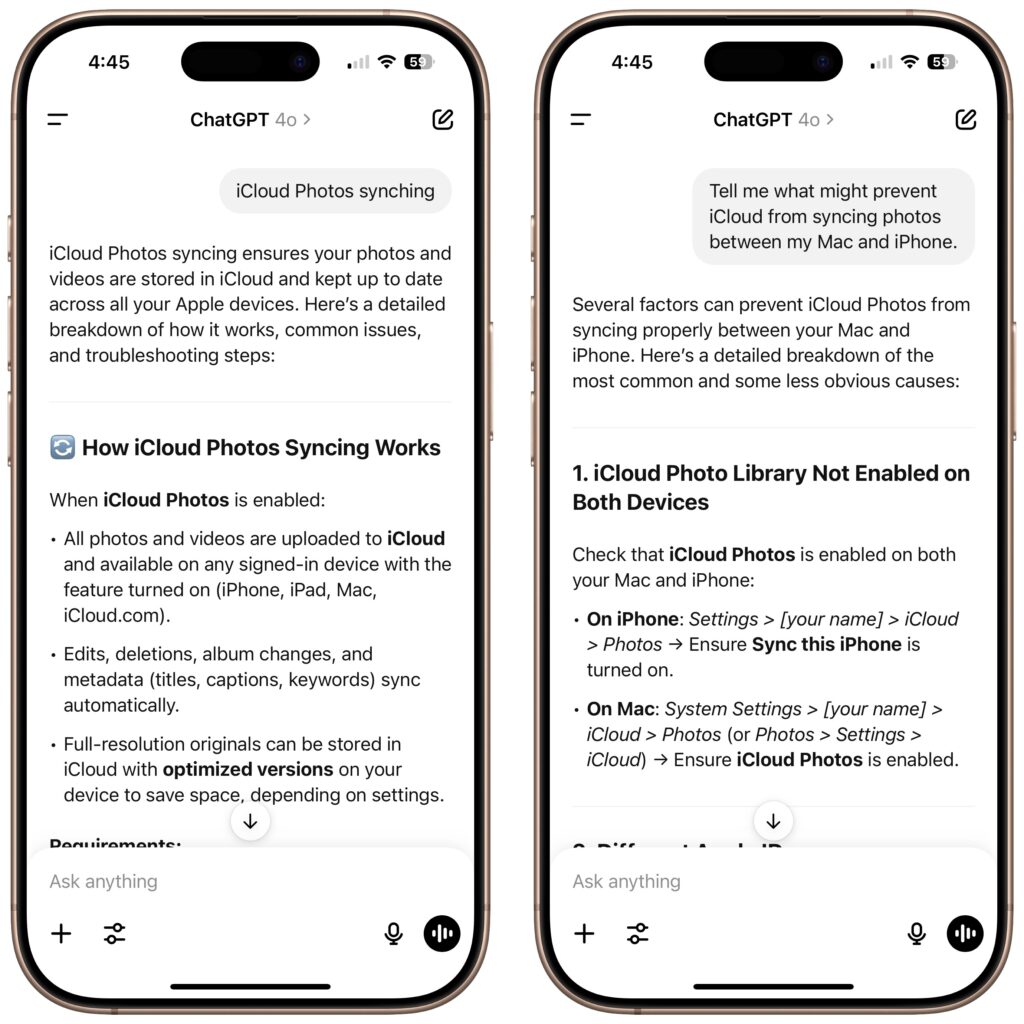
- Be specific and complete: Decades of search engine use push us toward short, focused search phrases with keywords that will appear in the results. In contrast, chatbots thrive on specificity and detail. For instance, prompting a chatbot with “iCloud photos syncing” won’t generate nearly as useful a response as “Tell me what might prevent iCloud from syncing photos between my Mac and iPhone.” Also, don’t shy away from negative prompting—tell the chatbot what not to include or consider in its response. You can even be specific about formatting the output as a bullet list, table, or graph.
- Every prompt is a conversation: We are accustomed to standalone searches, where, if the search fails, you must start over. You’ll achieve much better results with chatbots if you consider everything a conversation. Even responses to specific, detailed prompts may not fully address your question or could lead you to think of additional ones. Ask follow-up questions, clarify what you want to find out or accomplish, provide feedback, or redirect the conversation as needed. (For the ultimate chatbot conversational experience, try voice mode in the ChatGPT or Claude apps, where they talk back to you. It’s excellent for capturing ideas, refining your thinking, or just doing a brain dump.)
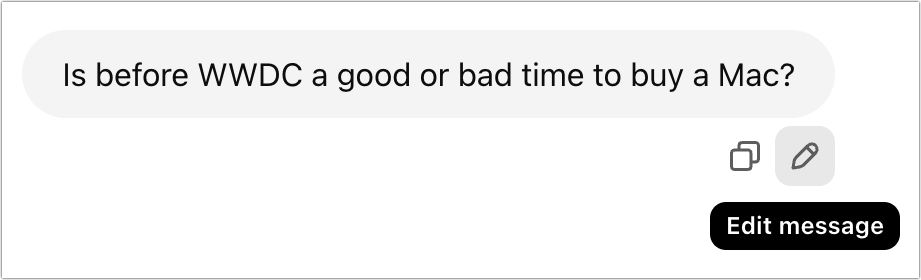
- Edit your last prompt: If the most recent response from a chatbot is entirely unsatisfactory, you may have better luck editing and resubmitting it rather than informing the chatbot that it has made a mistake. There’s usually an edit link or pencil button that appears when you hover over it.
- Context can help: Most chatbots maintain libraries of previous conversations, allowing you to search through them to find old ones easily. Because chatbot responses improve with more context, it can be helpful to return to one of those conversations when you want to explore that topic further. Similarly, if you’re asking a chatbot to create something similar to something you’ve already done, provide the previous work as an example.
- Ask it to role-play: Another way to increase context is to ask the chatbot to “act as” a particular type of professional, such as an editor, coach, marketer, or software developer. In essence, you’re asking the chatbot to respond in the context of a certain role. Conversely, it can be helpful to ask it to tailor its response as if you were a high school student, someone with a basic understanding of the topic, or an expert in the field.
- Know when to start over: Although context is key, chatbots have a limited memory, so long conversations can overwhelm what’s called the “context window.” If you notice the chatbot hallucinating, starting to repeat itself, or going off into the weeds, try saying, “Please summarize what we’ve discussed in a prompt I can use to continue working on this topic.” Then, copy that prompt into a new chat before continuing the conversation.
- Force Web searches as necessary: Most chatbots make it explicit when they are searching the Web, which means you can also tell when they aren’t searching and are thus relying on potentially outdated training data. If you want to ensure that you’re getting the latest information, tweak your prompt to start with something like “Search for…”
- Test its limits: Since every chatbot response is based on just what you say in the prompt, it won’t necessarily go as deep as you would like. Try asking it to critique its own output, generate multiple options, or present the best argument for different perspectives. You can even request it to be more cautious or more creative. It’s fine to challenge a chatbot in ways that would be socially inappropriate with another person.
- Save and reuse effective prompts: When you identify prompts that work particularly well for recurring tasks—such as generating meeting summaries, analyzing data, or drafting specific types of content—save them for reuse so you don’t have to start over each time.
- Don’t believe everything you read on the Internet. While chatbots are incredibly confident and often truly astonishing in what they can produce, it’s your responsibility to verify important facts and details (just as with human-created information, which isn’t necessarily any more trustworthy). The statistical models they use can lead to completely fabricated information. Although this is less true with Web searches, even there, they can combine information in ways that simply aren’t accurate.
- Try deep research: Bonus tip! Many chatbots offer a so-called deep research mode, which allows the chatbot to go off for 5 or 10 minutes to gather information, analyze it over multiple steps, and produce a much more comprehensive response. Deep research is too slow for a conversation, but it can provide a good foundation when you’re exploring a new topic that requires a lot of detail.
While AI chatbots are powerful tools, they work best when you think of them as collaborative partners rather than magical solutions. The key is experimentation—try different approaches, refine your prompting style, and don’t hesitate to push the limits of what they can do. Start with these fundamentals, but remember that becoming proficient is an ongoing process.
(Featured image by iStock.com/Memorystockphoto)
Social Media: Getting the most out of ChatGPT and Claude requires a different approach than using a traditional search engine. Learn ten essential tips for better prompting, from being conversational to leveraging context and even role-playing.