There’s an Internet saying: “If you’re not the customer, you’re the product.” The point is that, if you’re getting a service for free, the company providing it sees you not as a customer, but as a product to sell, generally to advertisers.
This is how Google, Facebook, and Twitter operate. They provide services for free, collect data about you, and make money by showing you ads. In theory, the more that advertisers know about you, the better they can target ads to you, and the more likely you’ll be to buy. Personalized advertising can seem creepy (or clueless, when it fails), but it isn’t inherently evil, and we’re not suggesting that you stop using ad-supported services.
This ad-driven approach stands in stark contrast to how Apple does business. Apple makes most of its money by selling hardware—iPhones, Macs, and iPads, primarily. Another big chunk of Apple’s revenue comes from App Store and iTunes Store sales, iCloud subscriptions, and Apple Pay fees. Knowing more about you, what Web pages you visit, what you buy, and who you’re friends with doesn’t help Apple’s business, and on its Privacy page, Apple says bluntly, “We believe privacy is a fundamental human right.”
Of course, once your data is out there, it can be lost or stolen—in June 2018, a security researcher discovered that the online data broker Exactis was exposing a database containing 340 million records of data on hundreds of millions of American adults. Ouch!
Let’s look at a few of the ways that Apple protects your privacy.
Siri and Dictation
 The longer you use Siri and Dictation, the better they work, thanks to your devices transmitting data back to Apple for analysis. However, Apple creates a random identifier for your data rather than associating the information with your Apple ID, and if you reset Siri by turning it off and back on, you’ll get a new random identifier. Whenever possible, Apple keeps Siri functionality on your device, so if you search for a photo by location or get suggestions after a search, those results come from local data only.
The longer you use Siri and Dictation, the better they work, thanks to your devices transmitting data back to Apple for analysis. However, Apple creates a random identifier for your data rather than associating the information with your Apple ID, and if you reset Siri by turning it off and back on, you’ll get a new random identifier. Whenever possible, Apple keeps Siri functionality on your device, so if you search for a photo by location or get suggestions after a search, those results come from local data only.
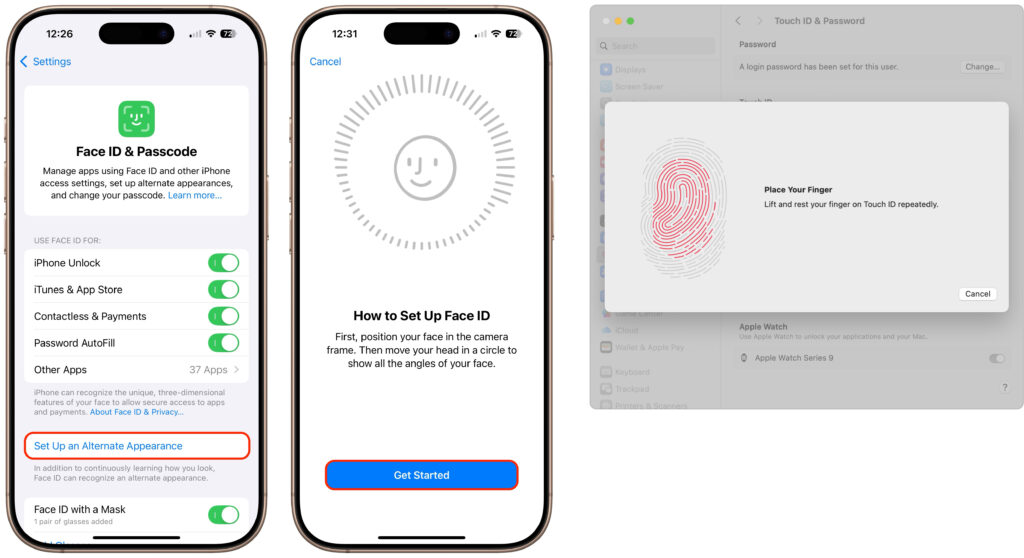
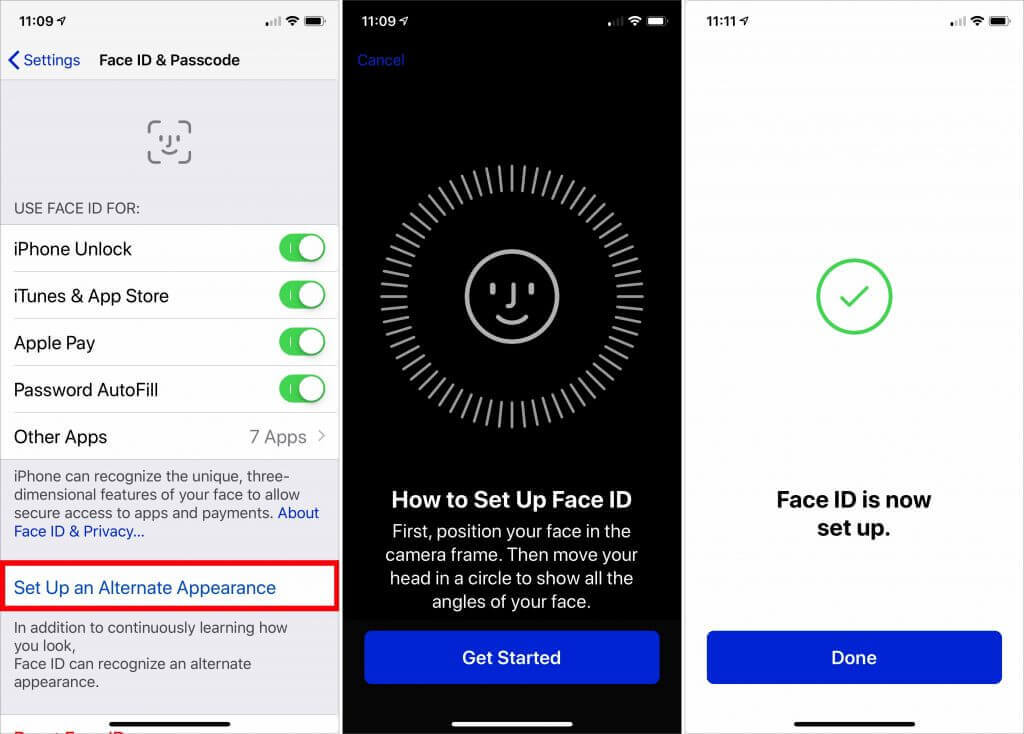
Touch ID and Face ID
 When you register your fingerprints with Touch ID or train Face ID to recognize your face, it’s reasonable to worry about that information being stored where attackers—or some government agency—could access it and use it for nefarious purposes. Apple was concerned about that too, so these systems don’t store images of your fingerprints or face, but instead mathematical signatures based on them. Those signatures are kept only locally, in the Secure Enclave security coprocessor that’s part of the CPU of the iPhone and iPad—and on Touch ID-equipped laptops—in such a way that the images can’t be reverse engineered from the signatures.
When you register your fingerprints with Touch ID or train Face ID to recognize your face, it’s reasonable to worry about that information being stored where attackers—or some government agency—could access it and use it for nefarious purposes. Apple was concerned about that too, so these systems don’t store images of your fingerprints or face, but instead mathematical signatures based on them. Those signatures are kept only locally, in the Secure Enclave security coprocessor that’s part of the CPU of the iPhone and iPad—and on Touch ID-equipped laptops—in such a way that the images can’t be reverse engineered from the signatures.
And, of course, a major goal of Touch ID and Face ID is to prevent someone from violating your privacy by accessing your device directly.
Health and Fitness
 People with medical conditions can be concerned about health information impacting health insurance bills or a potential employer’s hiring decision. To assuage that worry, Apple lets you choose what information ends up in Health app, and once it’s there, encrypts it whenever your iPhone is locked. Plus, any Health data that’s backed up to iCloud is encrypted both in transit and when it’s stored on Apple’s servers.
People with medical conditions can be concerned about health information impacting health insurance bills or a potential employer’s hiring decision. To assuage that worry, Apple lets you choose what information ends up in Health app, and once it’s there, encrypts it whenever your iPhone is locked. Plus, any Health data that’s backed up to iCloud is encrypted both in transit and when it’s stored on Apple’s servers.
App Store Guidelines
 A linchpin in Apple’s approach to privacy is its control over the App Store. Since developers must submit apps to Apple for approval, Apple can enforce stringent guidelines that specify how apps can ask for access to your data (location, photos, contacts, etc.). This isn’t a blanket protection—for instance, if you allow a social media app Facebook to access your contacts and location, the company behind that app will get lots of data on your whereabouts and can even cross-reference that with the locations of everyone in your contact list who also uses the service.
A linchpin in Apple’s approach to privacy is its control over the App Store. Since developers must submit apps to Apple for approval, Apple can enforce stringent guidelines that specify how apps can ask for access to your data (location, photos, contacts, etc.). This isn’t a blanket protection—for instance, if you allow a social media app Facebook to access your contacts and location, the company behind that app will get lots of data on your whereabouts and can even cross-reference that with the locations of everyone in your contact list who also uses the service.
In the end, only you can decide how much information you want to share with the likes of Google, Facebook, and Twitter, and only you can determine if or when their use of your details feels like an invasion of privacy. But by using Apple products and services, you can be certain that the company that could know more about you than any other is actively trying to protect your privacy.
Social Media: Many of the big Internet companies make their money by assembling a dossier of information about you and then selling advertisers targeted access to you. Luckily, that’s not true of Apple—here are a few of the ways Apple protects your privacy.
The post Being an Apple User Means You’re Not the Product appeared first on TidBITS Content Network.